Ebolas Stealer: A New Hybrid Threat in 2025
Published Feb 1, 2025
Introduction
During my research, I stumbled upon a new and comprehensive
malware named
Ebolas Stealer
in the underground. Unlike traditional infostealers, this malware
combines the capabilities of an
infostealer,
Remote Access Trojan (RAT), and
ransomware, making it a significant threat to individuals and organisations
alike.
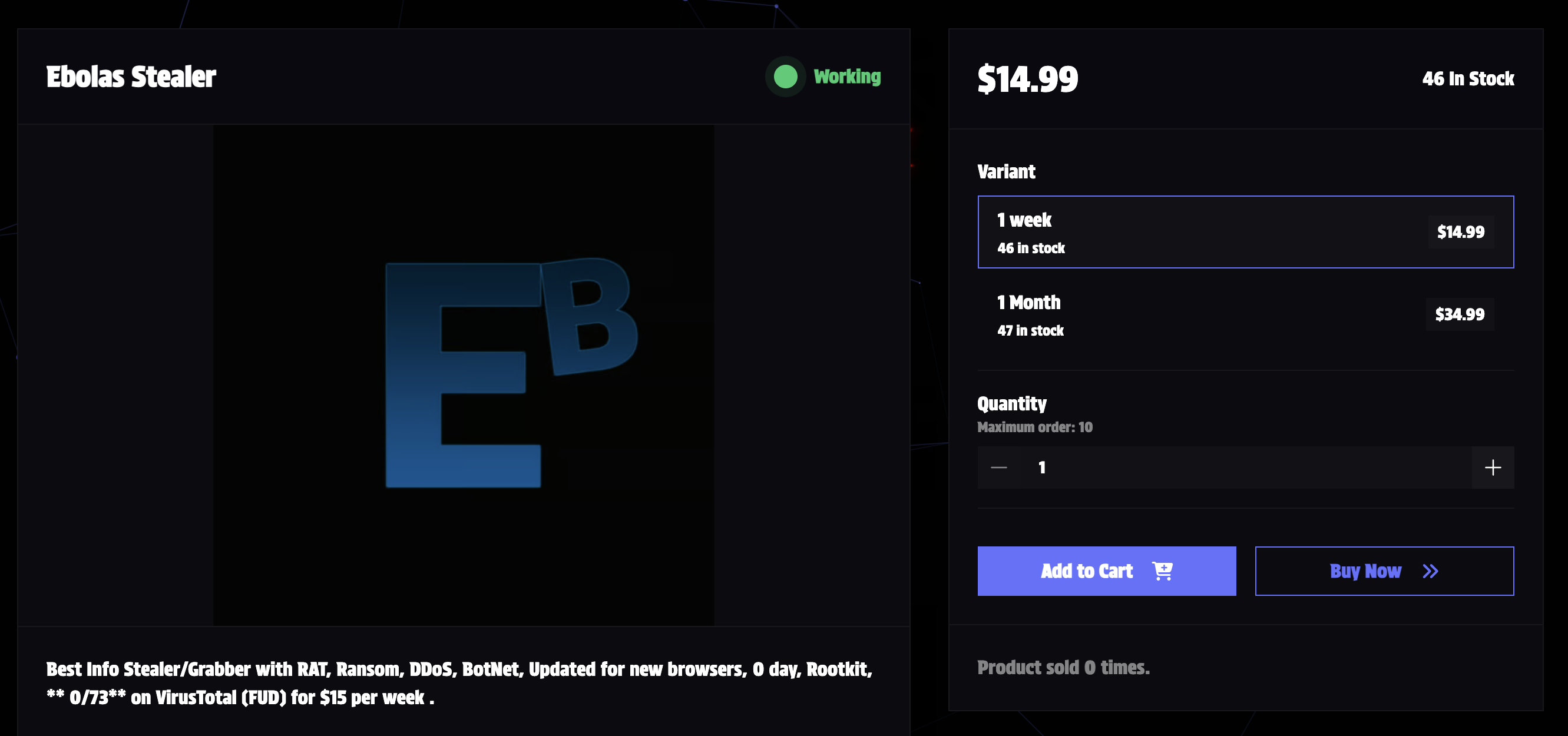
Ebolas Stealer
is currently being sold for just
$15 per week, and is marketed as a comprehensive tool for cybercriminals,
offering a wide range of malicious functionalities.
The malware author claims their product is fully undetectable
(FUD), with a detection rate of 0/73 on VirusTotal at the time of
writing. However, organisations should treat
Ebolas Stealer's
claims with caution. Regardless, its extensive feature set and low
cost make it a potent weapon in the hands of threat actors.
Tactics, Techniques, and Procedures (TTPs)
The following table outlines the Tactics, Techniques, and Procedures (TTPs) associated with Ebolas Stealer:
| Tactic | Technique ID | Name |
|---|---|---|
| Initial Access | T1566 | Phishing: Discord DM Spreading |
| Persistence | T1547 | Boot or Logon Autostart Execution |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Credential Access | T1555 | Credentials from Password Stores |
| Collection | T1005 | Data from Local System |
| Collection | T1113 | Screen Capture |
| Exfiltration | T1567 | Exfiltration Over Web Service |
| Impact | T1486 | Data Encrypted for Impact |
Real-World Impact
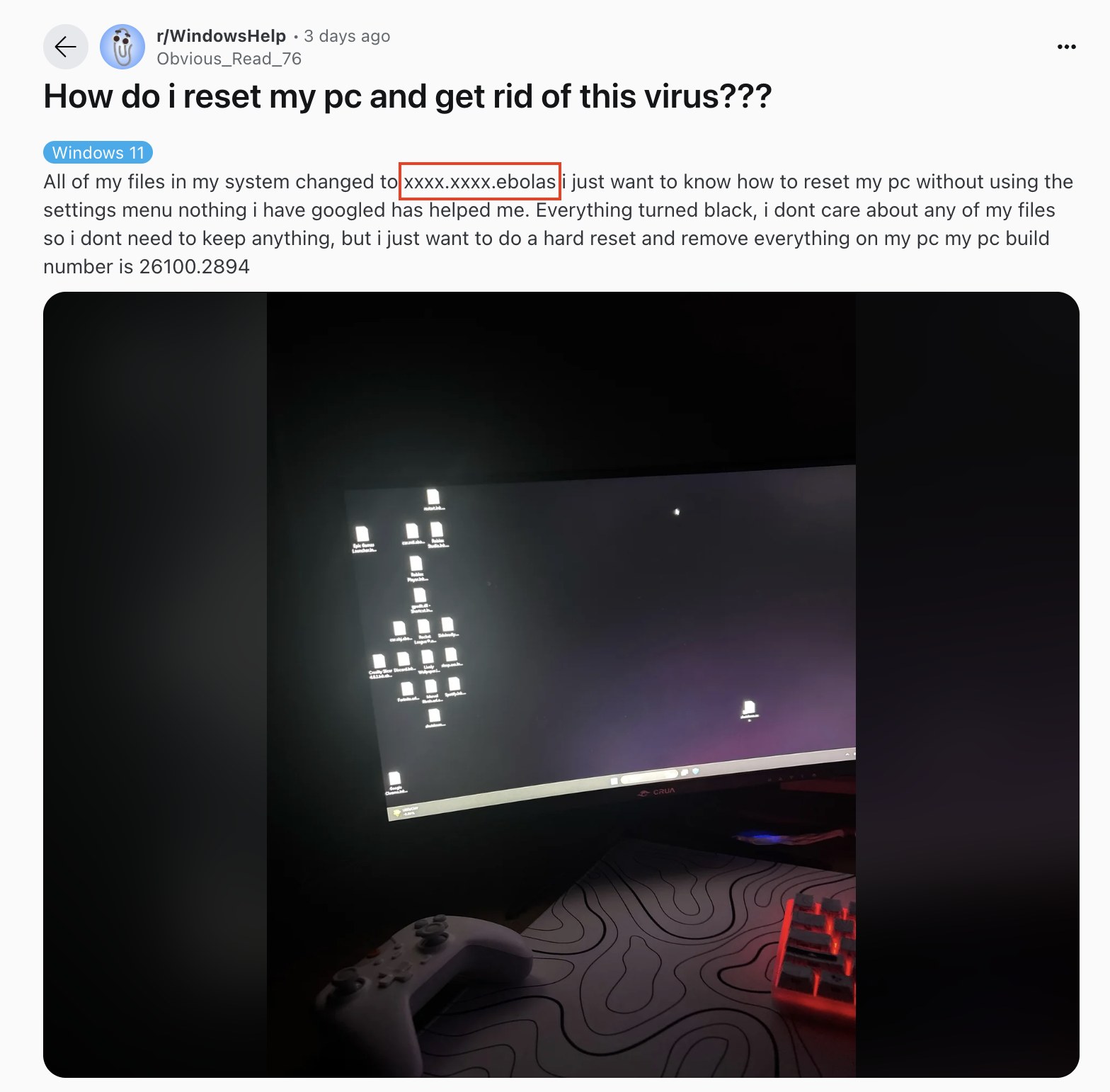
Evidence of Ebolas infections has already been observed in the wild. A recent Reddit post from r/WindowsHelp shows a user's system compromised by the malware, with their files encrypted and desktop.
Discovery
A detailed malware analysis is currently being conducted. This article will be updated with technical findings, indicators of compromise (IOCs), and additional details once the analysis is complete.
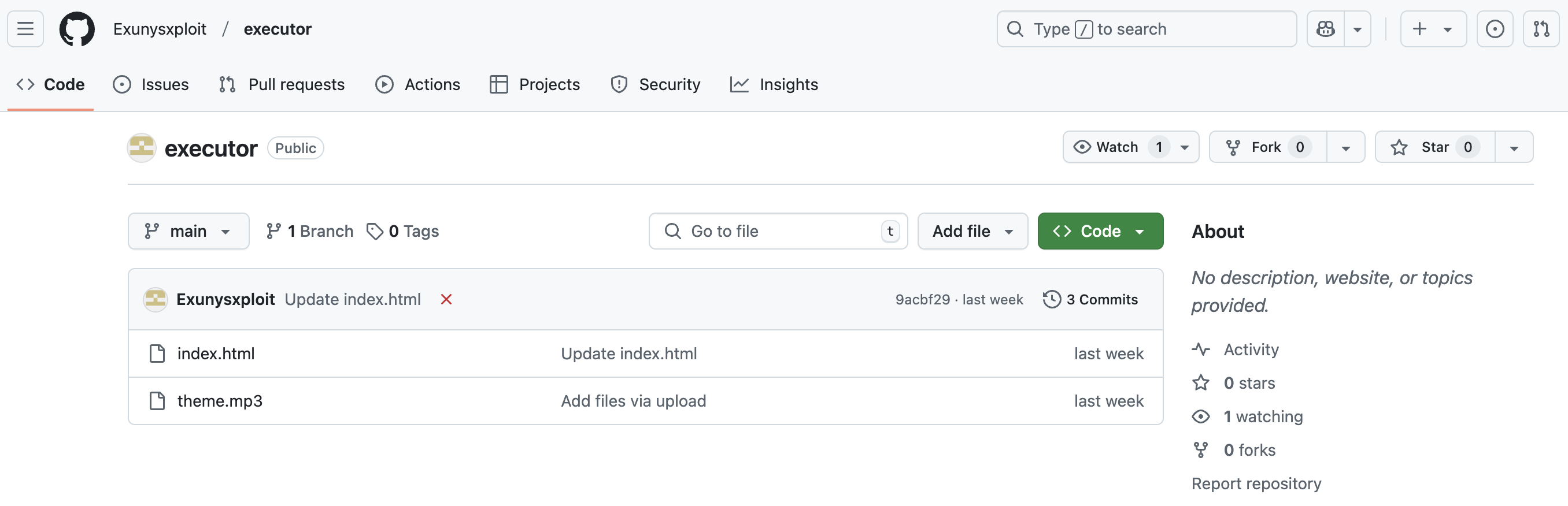
The first sightings of Ebolas Stealer were through GitHub, where it was being distributed masquerading as a popular Roblox cheat. The threat actors were impersonating Exunys, a well-known Roblox cheat developer, and distributing their malware as a fake version of Exunys' legitimate cheat tool. At the time of writing, the malicious executable has been taken down from GitHub, however I managed to get my hands on it and a detailed malware analysis is currently in progress.
Key Features and Capabilities
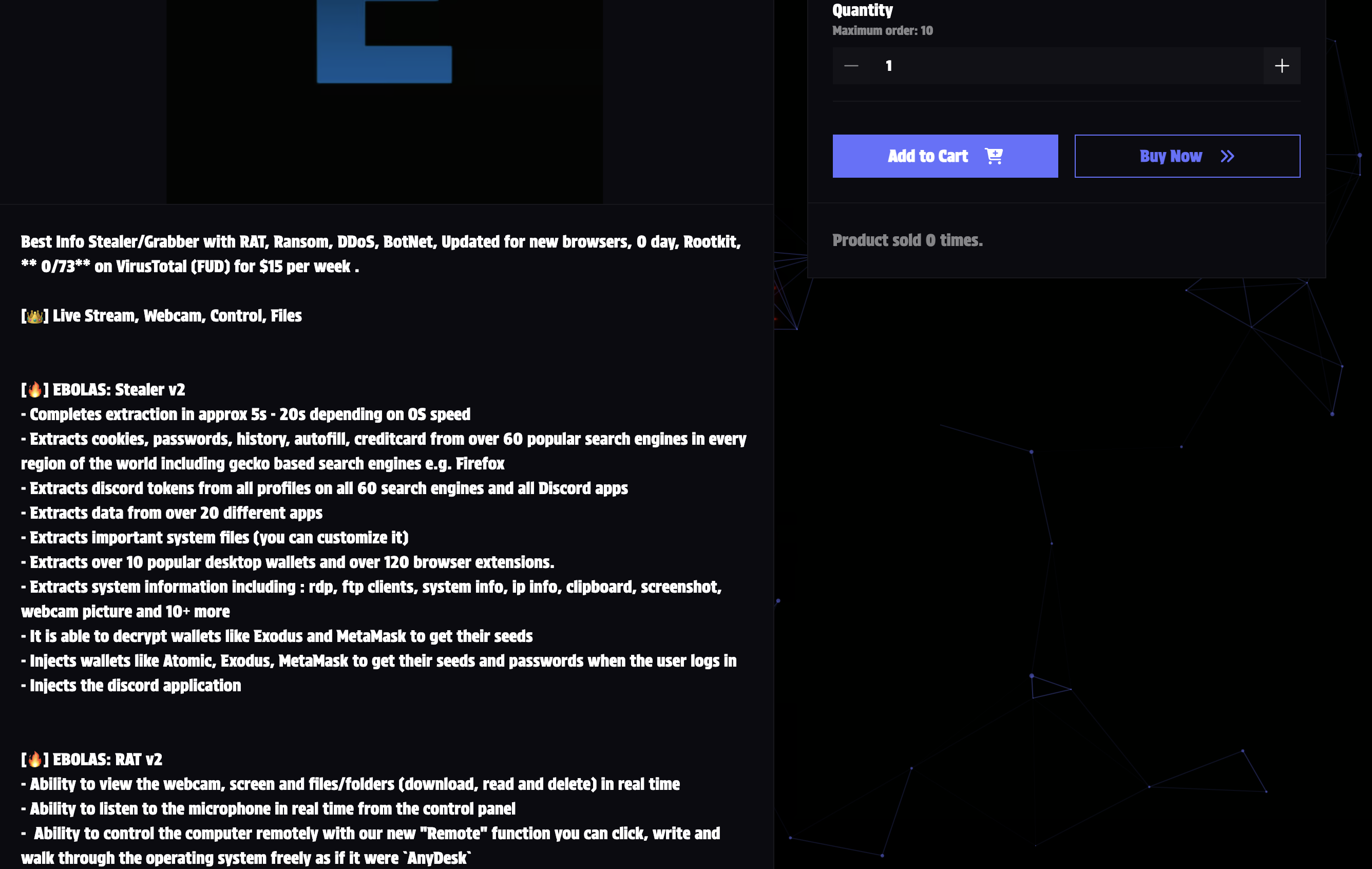
According to the malware author's advertisement, Ebolas Stealer offers an extensive set of features across three main components:
1. Information Stealing Capabilities
- Fast data extraction (5-20 seconds depending on system speed)
- Targets over 60 browsers, including Gecko-based engines
- Extracts cookies, passwords, history, autofill, and credit card data
- Discord token extraction across all profiles
- Data extraction from 20+ applications
-
Cryptocurrency wallet targeting:
- Supports 10+ desktop wallets and 120+ browser extensions
- Decryption capabilities for Exodus and MetaMask seeds
- Injection-based theft for Atomic, Exodus, and MetaMask
- System information collection including RDP, FTP clients, IP info, clipboard data, and webcam capture
2. Remote Access Features
- Real-time webcam and screen viewing
- Live microphone monitoring
- AnyDesk-like remote control functionality
- Live shell access with real-time command execution
-
System control commands including:
- Volume control including screamer functionality
- Real-time system information monitoring
- Over 40 different command options available
3. Ransomware Capabilities
- System lockdown with custom messages
- Advanced file encryption inspired by LockBit ransomware, claiming speeds of up to 100k files per minute
- Disk overwriting functionality
- DDoS attack capabilities
Additional Features
- Web-based control panel requiring no additional software
- Privilege escalation using claimed 0-day vulnerabilities
- Python project infection capabilities
- Chromium browser protection bypass
- Self-spreading through Discord DMs
- Discord notification system for new infections
- BotNet functionality for mass command execution
- Claimed compatibility with CIS countries
Available Commands (so far)
-
.lockdown (message)- Closes and locks the operating system with a customizable message -
.encrypt / .decrypt (key)- Encrypts all system files using advanced techniques inspired by LockBit ransomware, capable of encrypting over 100k files per minute -
.nuke- Overwrites the entire main disk of the operating system making it impossible to boot again -
.ddos (arg) (arg) (arg)- Allows sending a denial of service attack to an IP or website -
.screamer- Displays a screamer for 3 seconds with the volume at maximum -
.gdi_troll- Creates random visual effects on the screen with sound (infinite duration) -
.hell_rainbow- Displays an infinite hell rainbow effect -
.waves- Creates an infinite wave effect on the screen -
.corrupt_screen- Simulates infinite screen corruption effects -
.error_spam- Floods the screen with error icons indefinitely -
.nuke_gdi- Combines GDI effects with system destruction (requires admin, affects motherboard level)
RAT Dashboard
The following screenshots showcase various aspects of the Ebolas Stealer control panel:
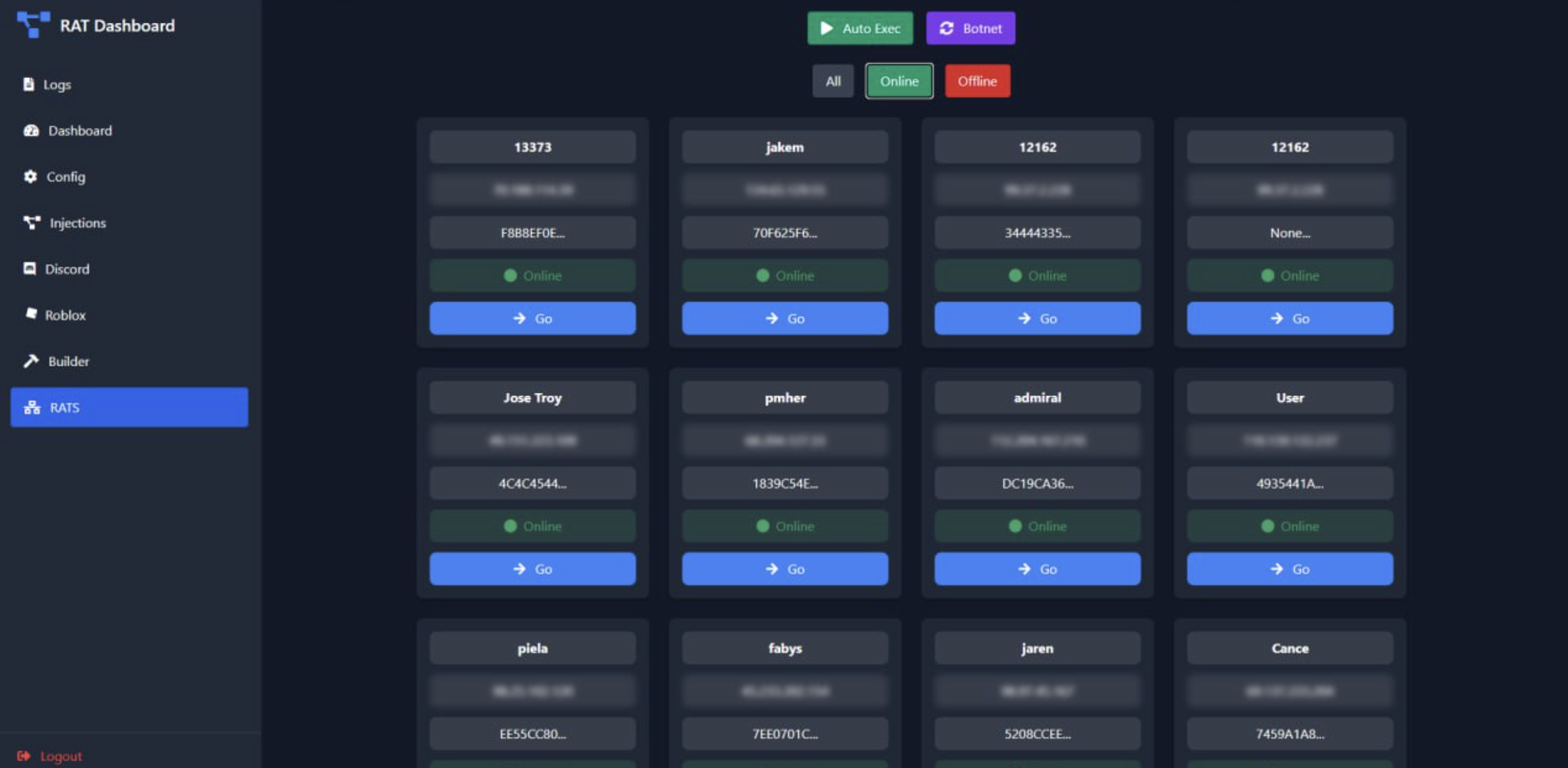
The RAT dashboard displays a grid of infected systems, each showing the victim's identifier and their online status. Each card includes a unique machine ID and a "Go" button that allows the attacker to establish a remote connection to the compromised system. The interface also includes filtering options to view all victims, only those currently online, or offline systems.
Discord and Roblox Stealer
The following screenshots showcase various aspects of the Ebolas Stealer Discord and Roblox dashboards:
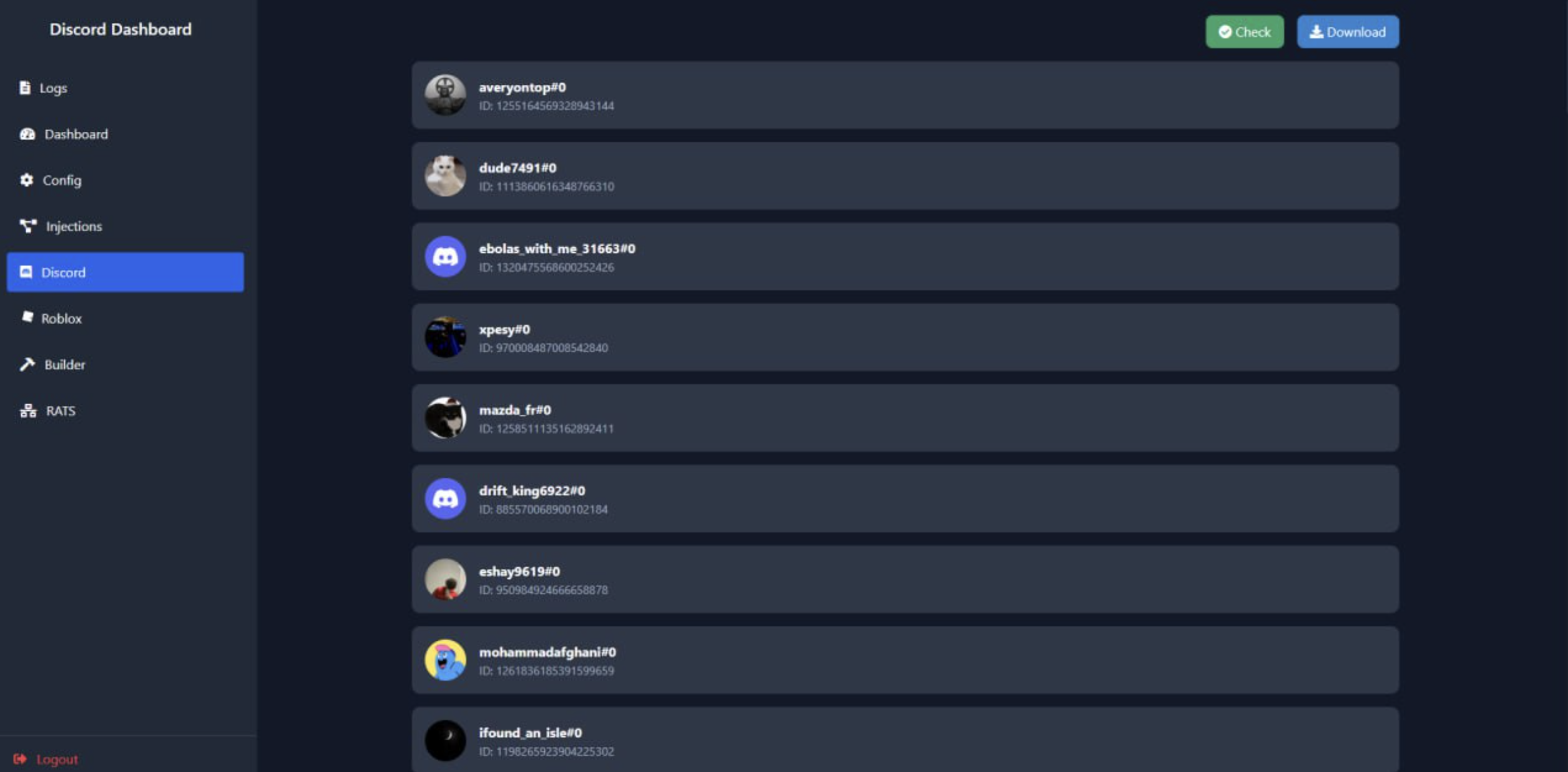
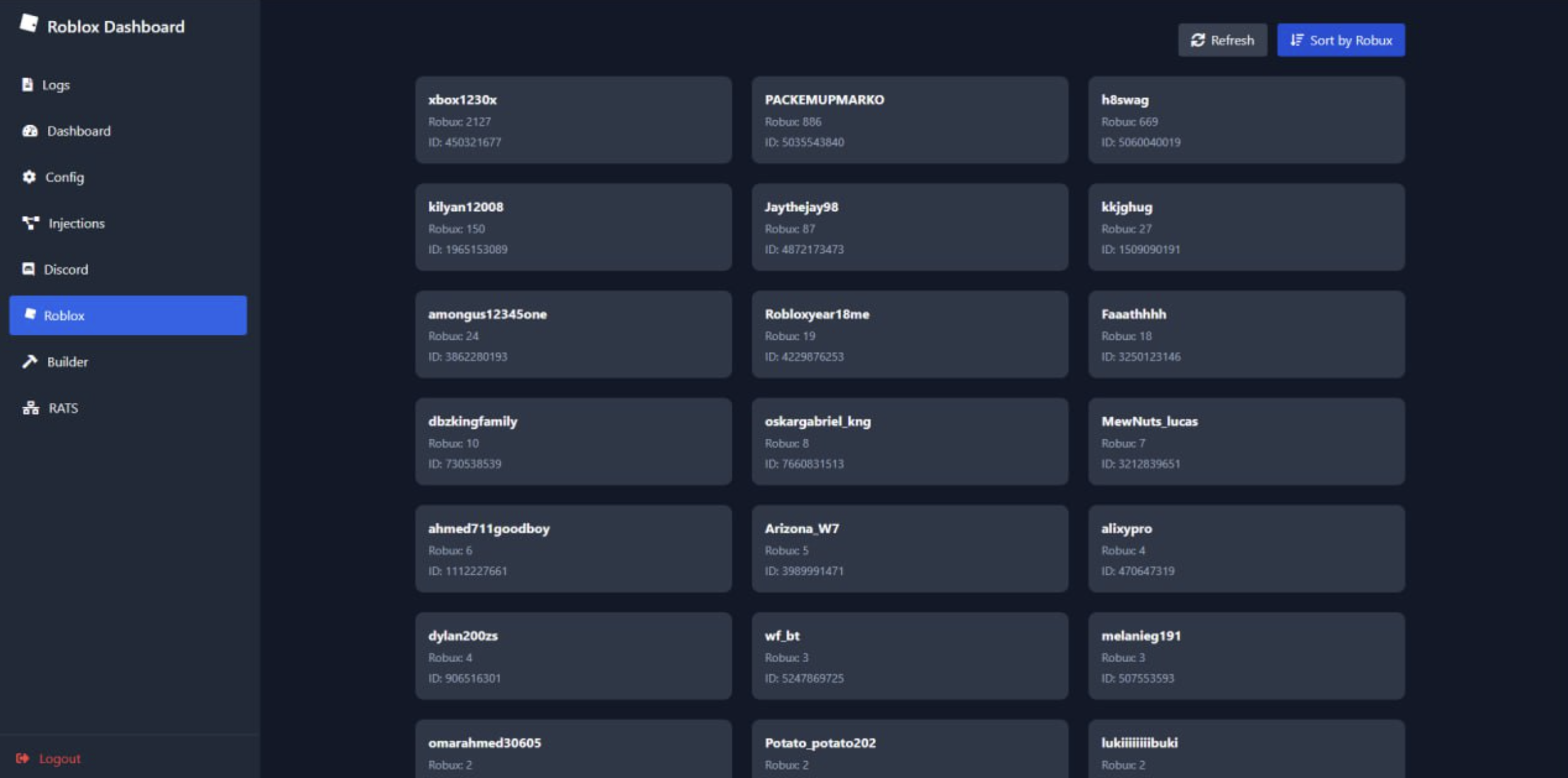
The Discord and Roblox dashboards provide an overview of compromised accounts. The interface displays a list of infected users, showing their account details and potential valuable assets. For Discord, this includes user tokens and account information, while the Roblox tab focuses on tracking accounts with potentially valuable in-game items or currency.
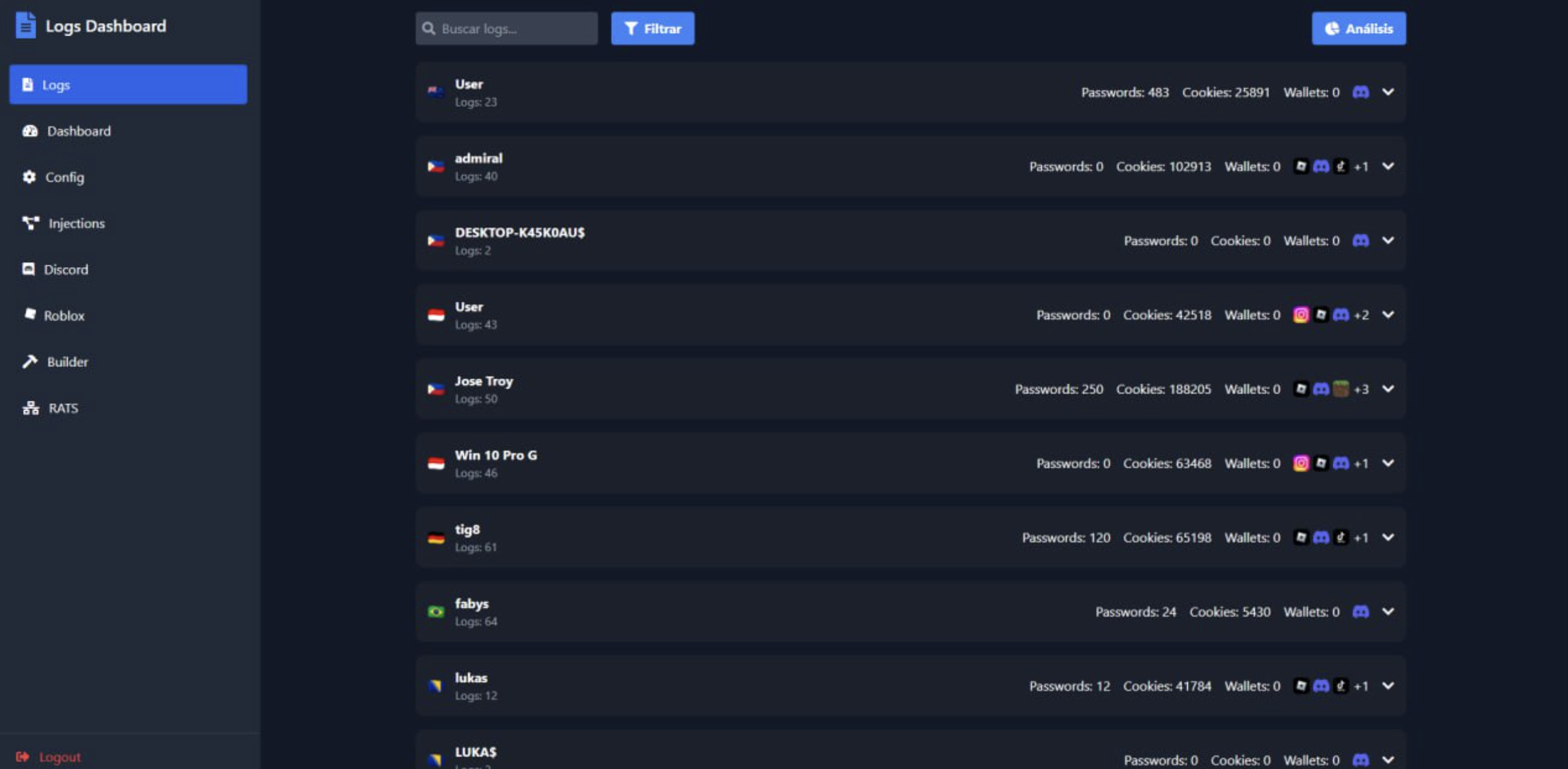
Logs
The following screenshots showcase various aspects of the Ebolas Stealer logs:
Remote Access Capabilities
The following screenshots showcase various aspects of the Ebolas Stealer infected system:
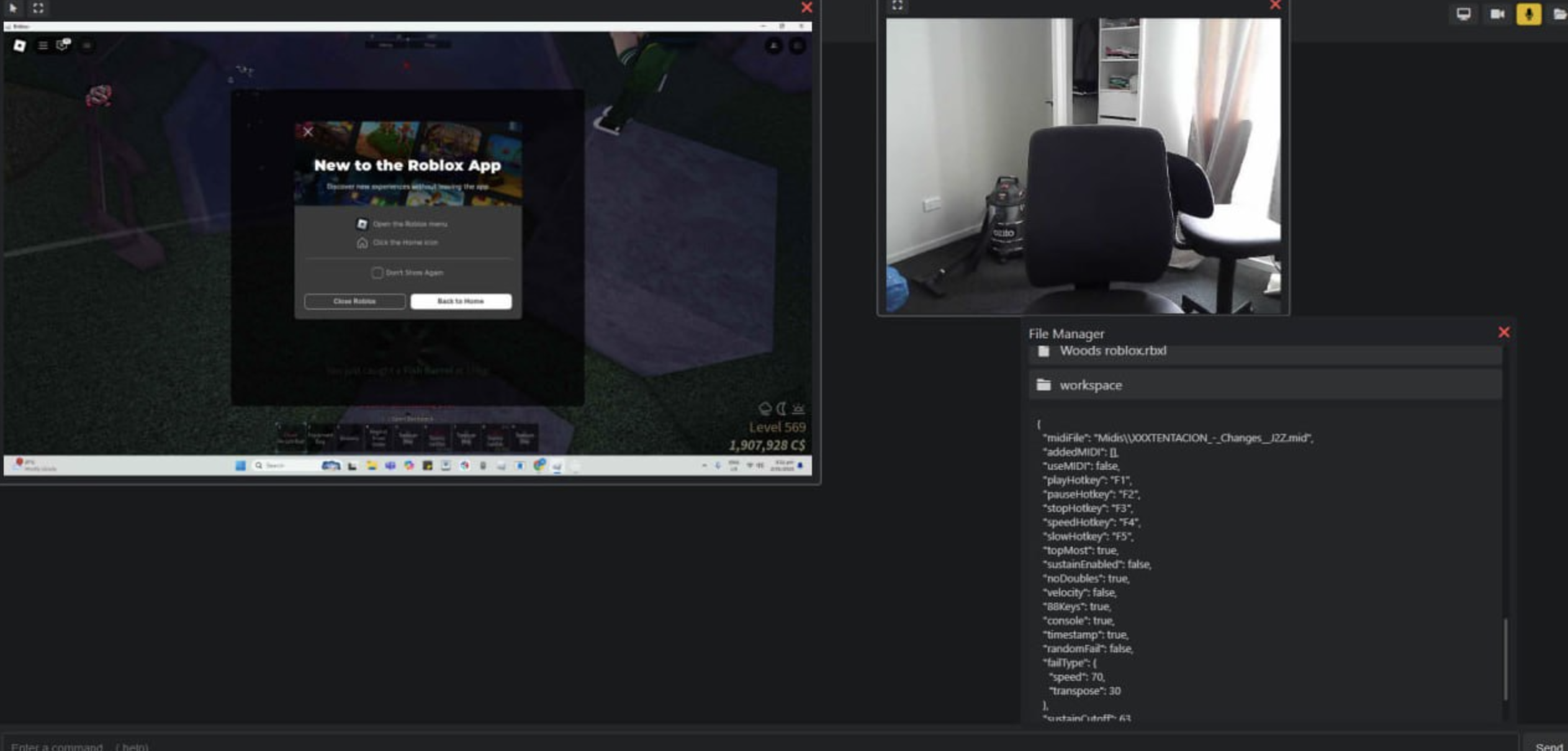
The screenshot demonstrates the Remote Access Trojan (RAT) capabilities of Ebolas Stealer. Once a system is infected, the malware enables unauthorized access to the victim's webcam and microphone, allowing real-time surveillance. The interface also provides access to the victim's file system, enabling the attacker to browse and manipulate files on the compromised machine.
Ransomware Note

When the ransomware component is activated, victims are presented with this lock screen featuring the Ebolas branding. The interface displays a simple message informing users that their files have been encrypted, along with instructions for contacting the attackers. The minimalist design with its dark theme and geometric pattern background appears to be inspired by modern ransomware families, aiming to create a sense of professionalism despite its malicious nature.
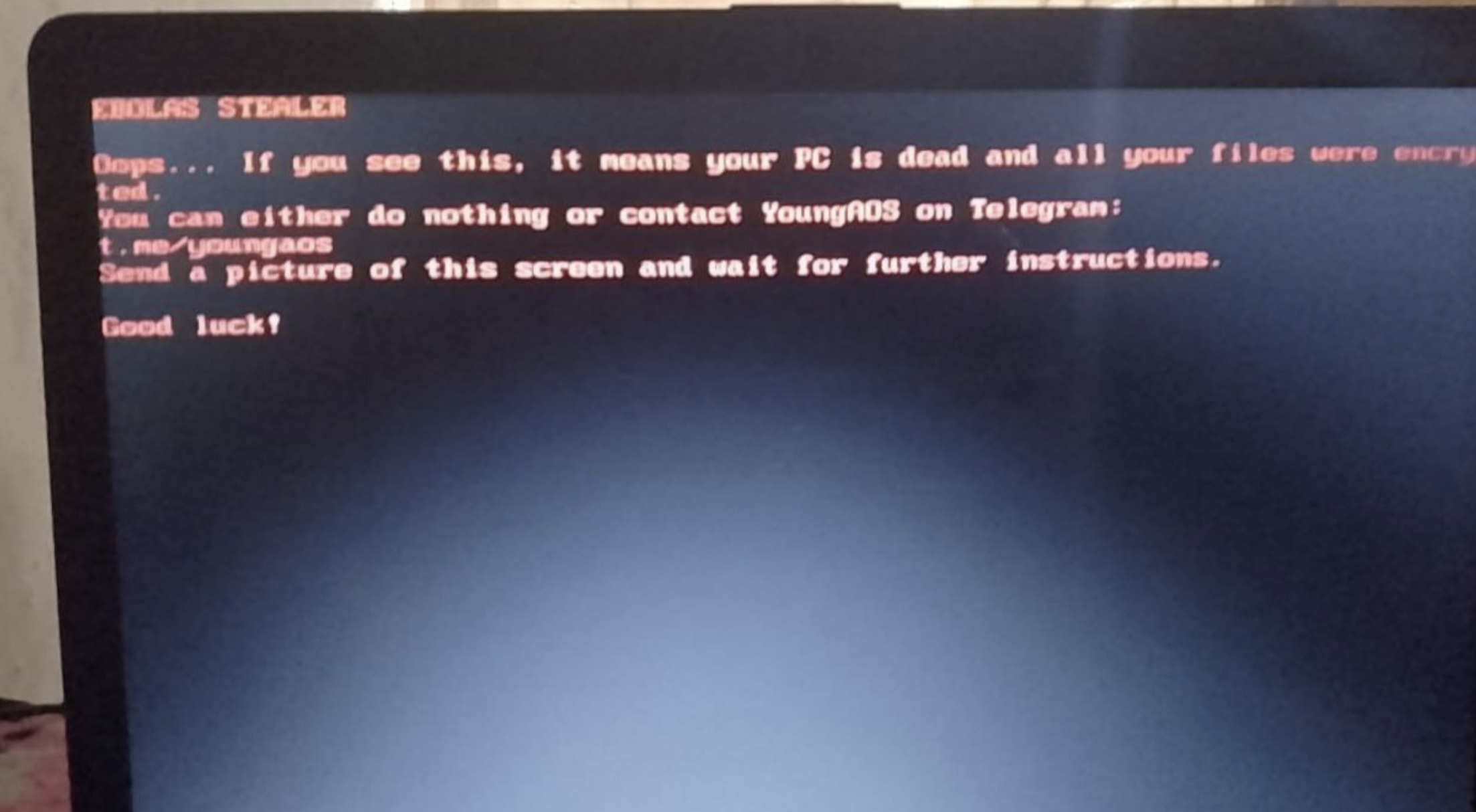
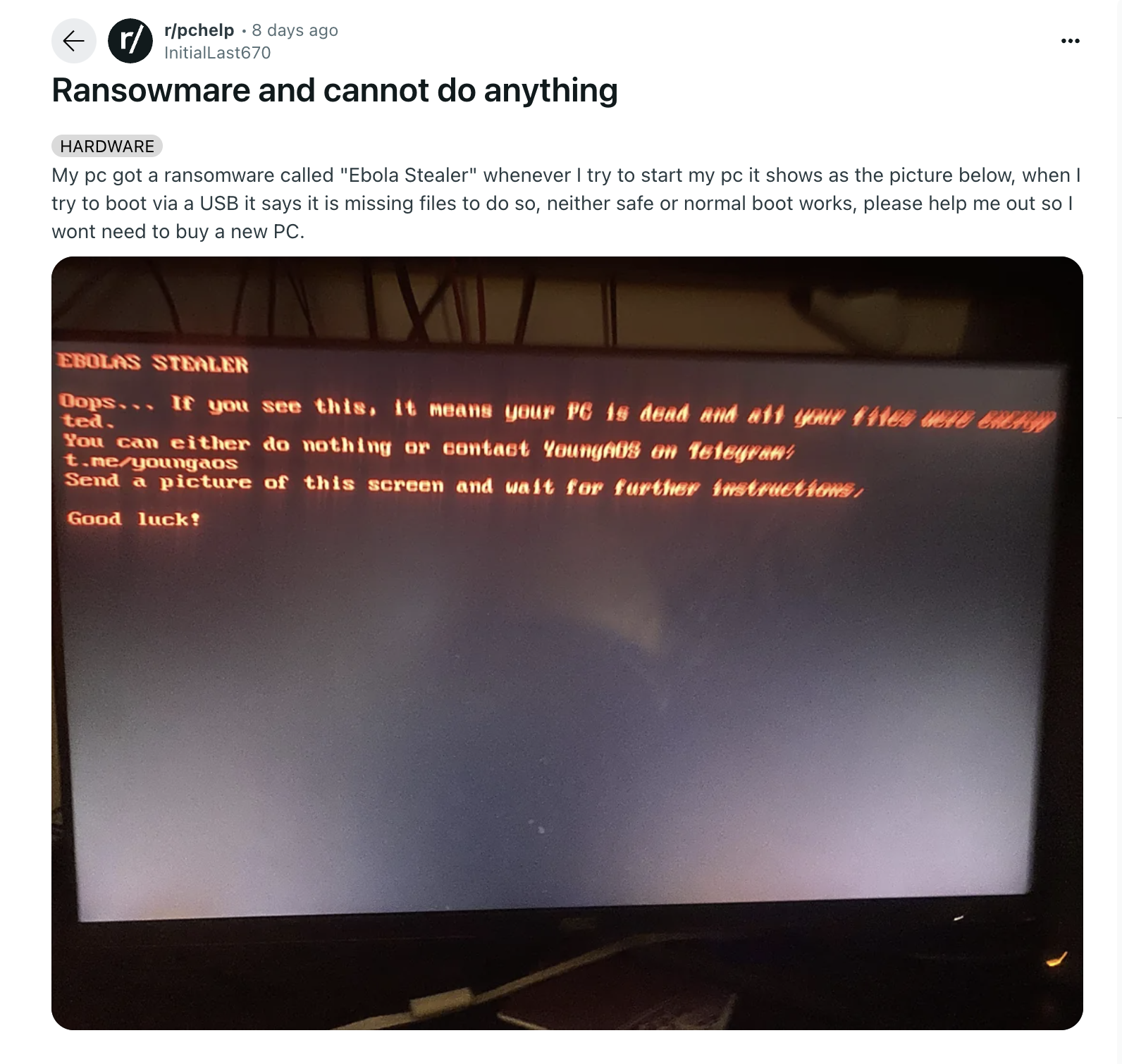
The ransomware also modifies the system's boot process to display this text-based ransom note during startup. Using a classic DOS-style interface, it informs victims that their PC is "dead" and their files are encrypted. The message includes contact instructions via Telegram for potential recovery, demonstrating how the malware maintains persistence even through system reboots.
Builder Interface
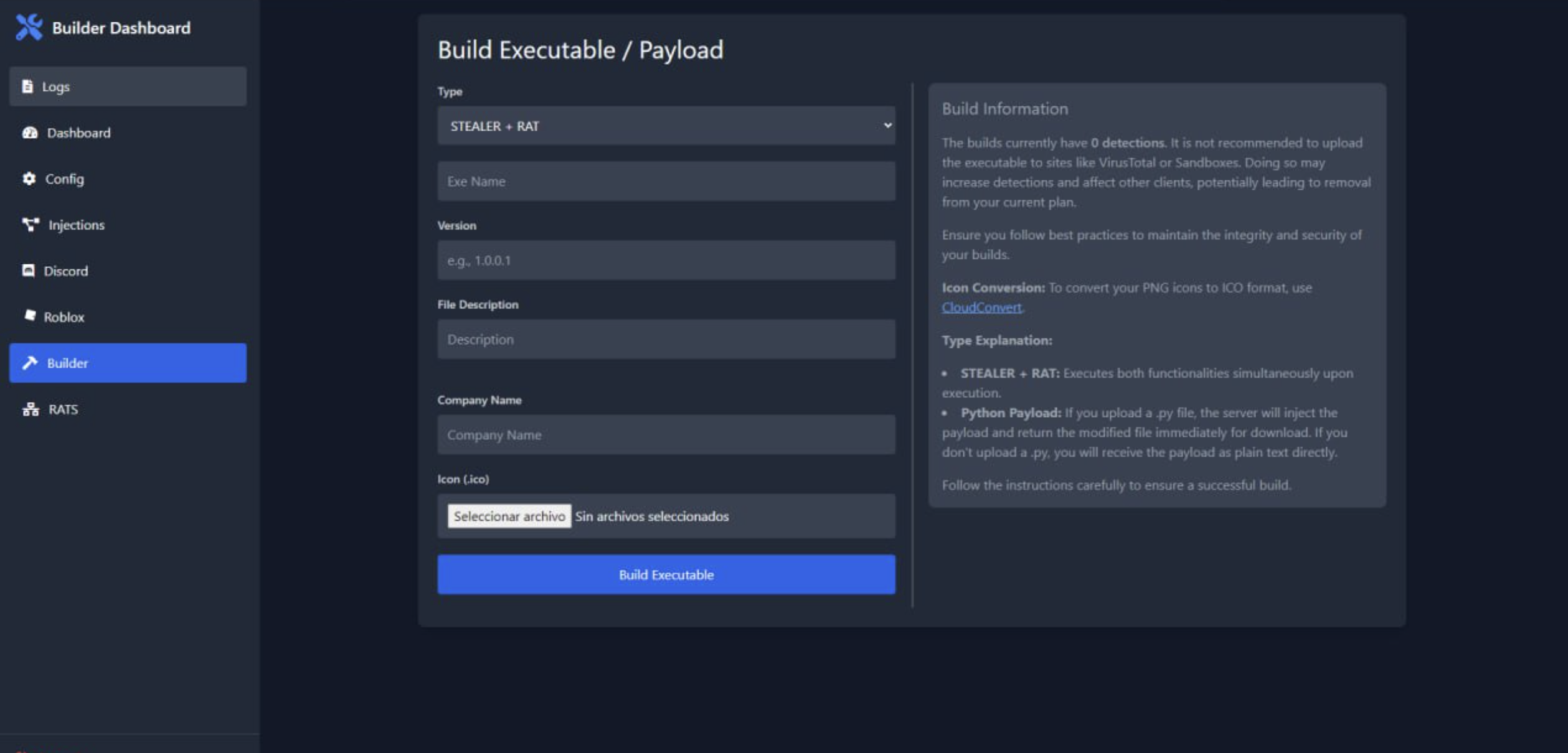
The builder interface provides options for customizing the malware payload. Users can select between different build types, including combined STEALER + RAT functionality. The interface allows configuration of executable properties such as name, version, company details, and custom icons. A warning message indicates the build has zero detections while cautioning against uploading to scanning services to maintain this status. The builder also supports Python payload injection for additional customization.
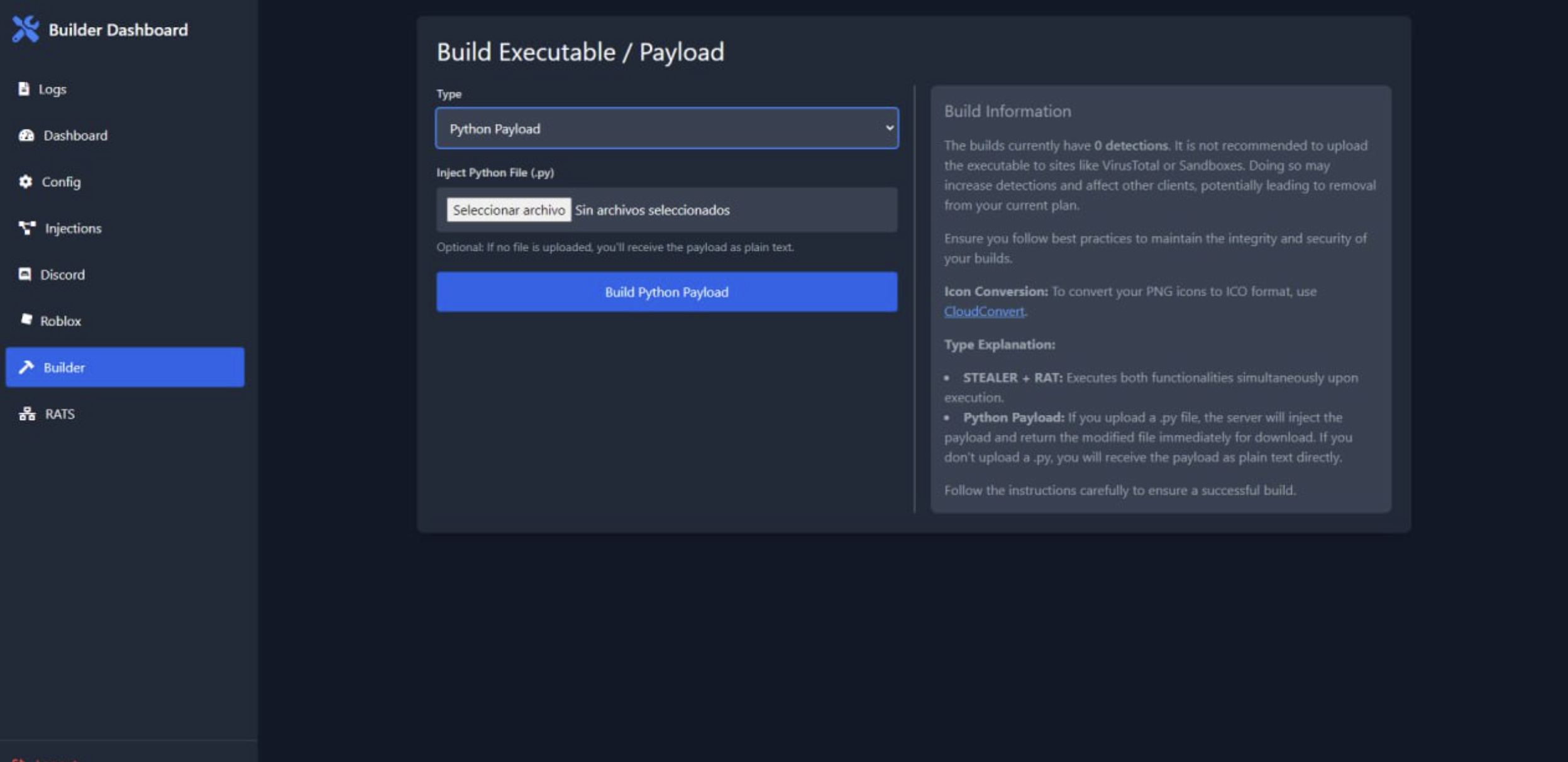
The builder interface features a Python payload injection capability. Users can upload a .py file which will be automatically injected with the malware payload, or receive the payload as plain text if no file is provided. The build information panel warns that builds currently have zero detections and advises against uploading to scanning services like VirusTotal or sandboxes to maintain this status.
Config Interface

The configuration panel shows two main sections: Discord Settings and File Filter Settings. The Discord section includes options for notifications, RAT functionality, and a spreading mechanism with a "Send to DMs + Block" mode. The File Filter Settings below allow operators to specify target files by name and extension, enabling selective data theft. These settings demonstrate the malware's focus on Discord platform exploitation and targeted file exfiltration.
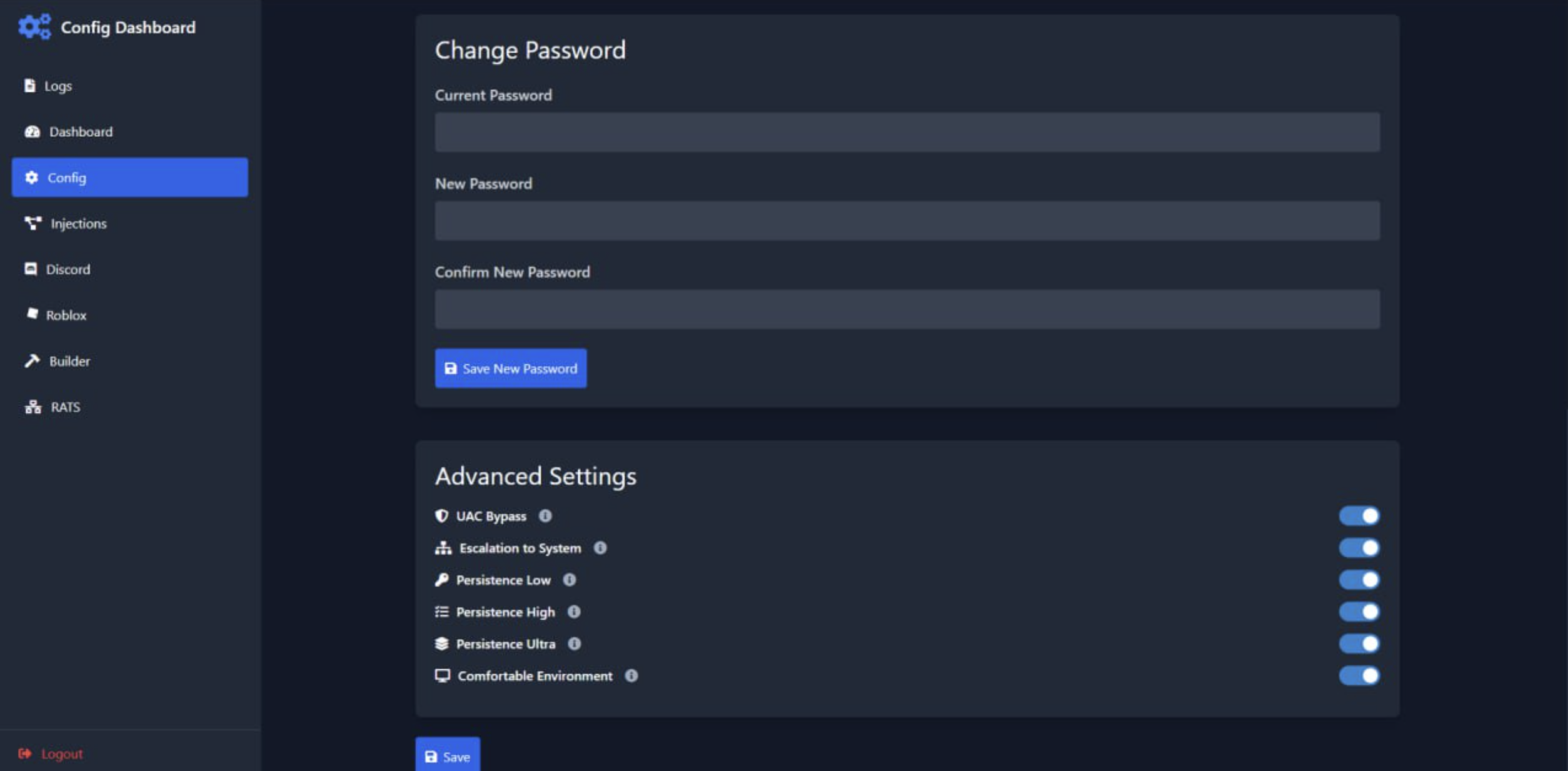
The Advanced Settings panel reveals the malware's persistence mechanisms. It includes options for UAC bypass, system privilege escalation, and three levels of persistence (Low, High, and Ultra) to maintain access to infected systems. The "Comfortable Environment" setting likely refers to anti-analysis features. These settings demonstrate the malware's focus on maintaining long-term access while evading detection and removal attempts.
Anti-Analysis Features

According to the malware author's claims, Ebolas implements anti-analysis measures including honeypots specifically targeting malware researchers. These allegedly include fake injection points, decoy links, and even deliberately leaked builds with simulated backend services. These traps are designed to waste researchers' time and gather intelligence on analysis attempts. However, these claims should be treated with skepticism as they have not been independently verified.
Recommendations
Organizations should consider the following measures to protect against this type of threat:
- Implement robust endpoint detection and response (EDR) solutions to detect and prevent malicious activities
- Enable multi-factor authentication (MFA) for all critical accounts, especially cryptocurrency wallets and Discord
- Regularly backup critical data and store backups offline to mitigate ransomware impact
- Monitor for suspicious process creation and persistence mechanisms
- Train users to recognize social engineering attempts and suspicious files
- Implement network segmentation to limit lateral movement capabilities
Conclusion
Ebolas Stealer represents a concerning evolution in malware development, combining infostealer, RAT, and ransomware capabilities into a single, affordable package. Its extensive feature set, anti-analysis measures, and low price point of $15/week make it particularly dangerous, as it lowers the barrier to entry for potential threat actors.
The malware's multi-layered approach to persistence, distributed infrastructure with rotating domains, and claimed anti-analysis capabilities demonstrate a level of sophistication that warrants attention from security professionals. While some of the advertised features remain unverified, the comprehensive nature of this threat highlights the ongoing need for robust security measures and continuous monitoring of emerging malware trends.